Think and do like the enemy
To take down the l33k3rs, we need to be able to think like they do, and be able to do what they can do.
L33k3ers most recent Hack
The l33k3rs have infiltrated the main dessert database (A database very important to the cyber house for obvious reasons) and have added leeks to all of the dessert recipes! They have defaced the main website with the l33k3rs name.
Alice and Bob have collected the photographic evidence
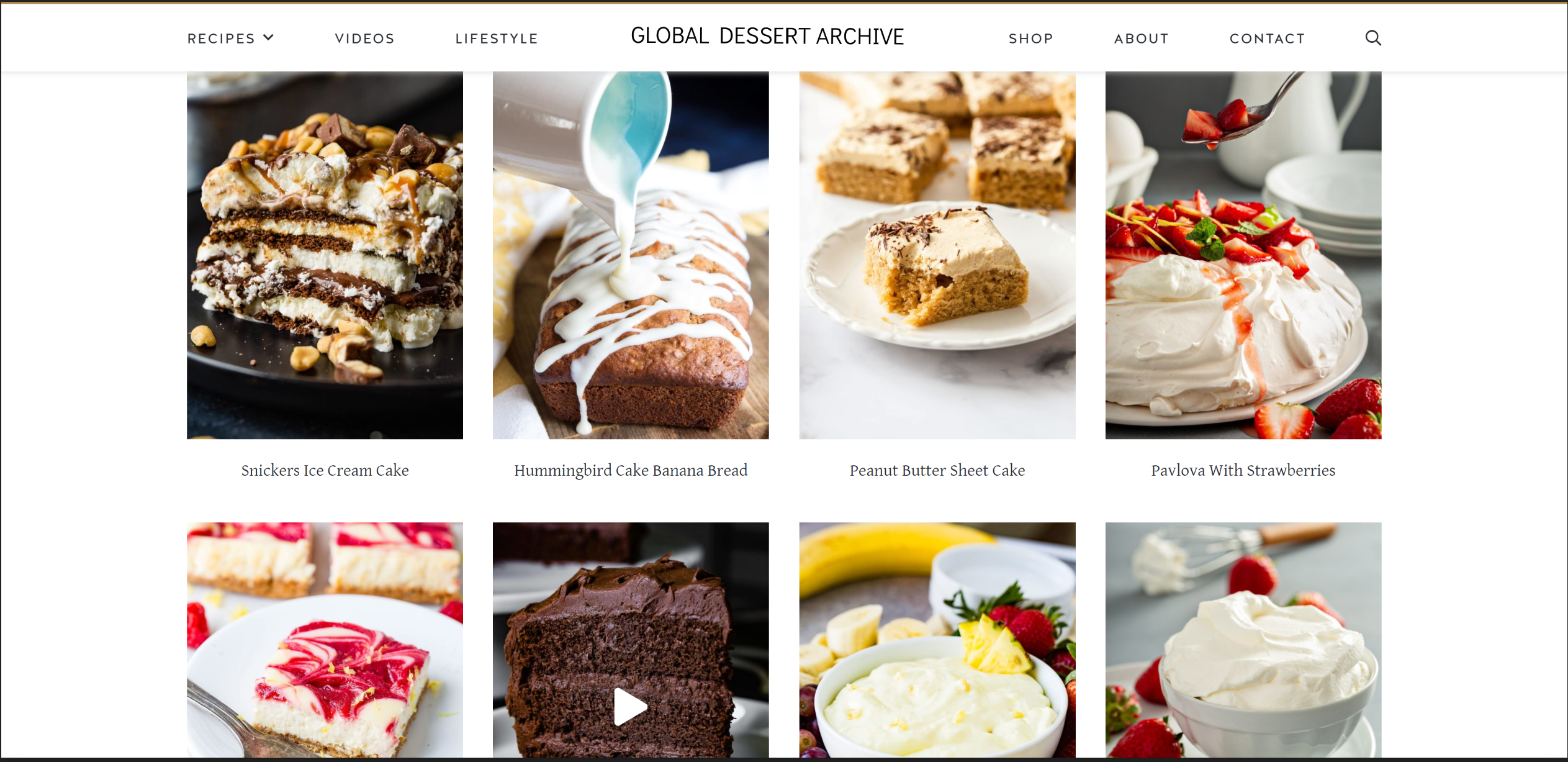
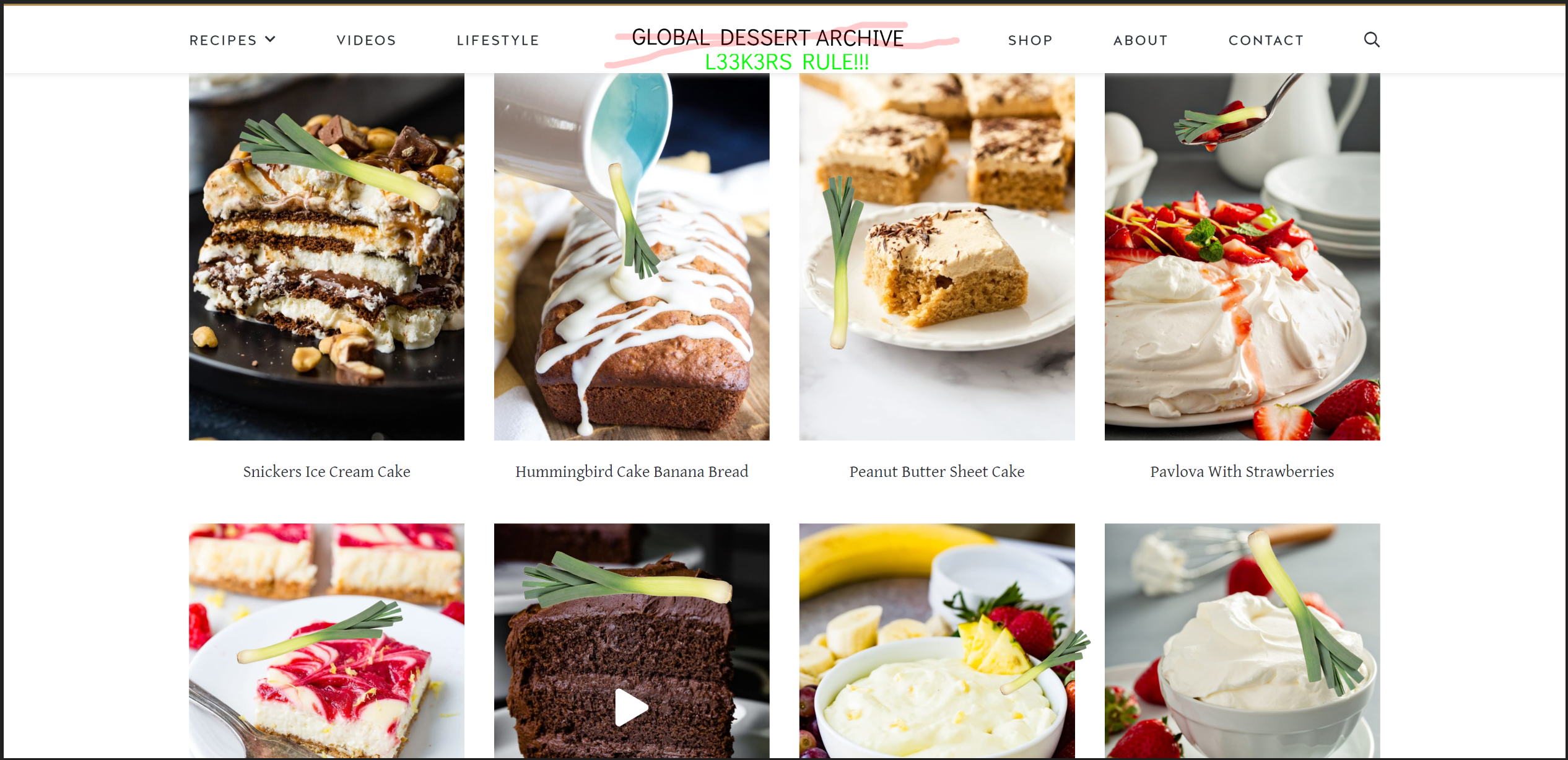
Horrible!
Today you will be taken through a series of exercises to develop your skills so you are able to figure out how the L33k3rs were able to hack into the dessert database! First, we will begin with learning bash.
Intro to bash
In the Cyber House, Alice and Bob have created an “Intro To Bash” training grounds, but they suspect that it has been infiltrated by the l33k3rs. However, they don’t have any proof.
Access the training grounds here to begin the training and find proof that the l33k3rs have infiltrated the training grounds.
Web infiltration Mission
.jpg)
The Global Dessert Vault developers have provided us with a sample copy of their website. They suspect that an old, unprotected file upload page is the culprit, but they can’t figure out how the l33k3rs managed to use the page to deface the main website.
Take a look and see what you and the rest of the team can learn from the file upload page here.
Here is a link to the page that may be helpful in your mission to find out how the L33k3rs l33ked our page! Good Luck!
Bug Bounties

In the future, the Gloabl Dessert Vault has decided to hire Bug Bounty Hunters to stop groups like the l33k3rs from gaining access to the Global Dessert Vault, and they would like your help!
But first, you need to know what a bug bounty hunter does, and how they do it. You should also probably know what a bug is! A bug, is an accidental problem within a program that might not be obvious to its creators, but can be exploited by hackers, like the l33k3rs, right under the programmer’s nose!
Originally, the term bug meant an actual insect had made its way into the computer and was stopping it from working! Computers are too small for that now though.
Bug bounty hunters are people who will go onto a program, with permission from the owner, and search for these exploitable problems, and are paid a bug bounty for every one they find!
Here’s an activity created by Google to help teach you about one of the most common bugs on the web, known as Cross-Site Scripting, or XSS.
Access the game here
Go here to learn more about bug bounty hunting jobs.