Victory!
Congratulations!
By executing the nanobot kill code, you have successfully defeated the L33k3rs!
They will no longer be a threat to the Global Dessert Database, and all of your favorite desserts are saved!
Alice and Bob are incredibly proud, and they thank you for your brave efforts.
So What Did We Actually Do This Week?
We know this week has been a bit confusing at times, but that’s because you guys did some really cool, really high-level stuff! To finish off our week, let’s break down what we did by comparing it to the real world.
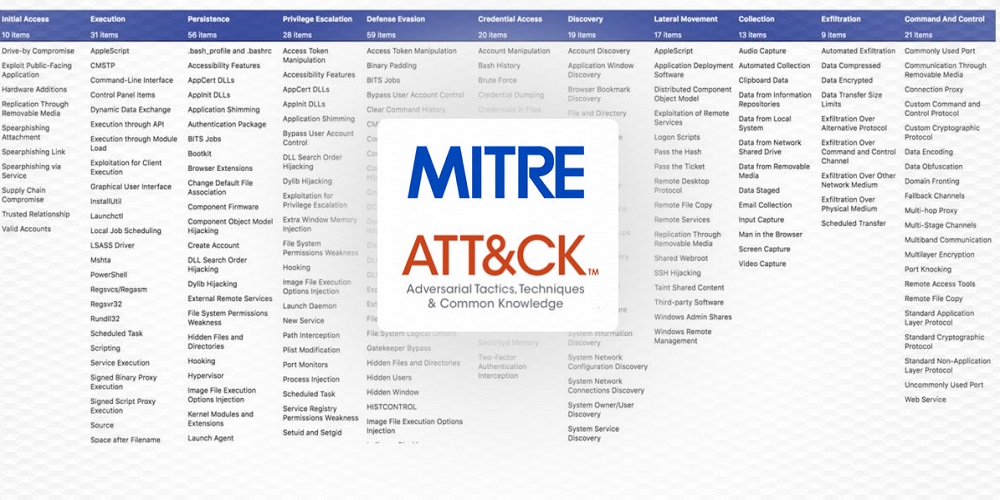
There’s this thing called the MITRE Att&ck Framework. Basically, it outlines everything you need to know about cybersecurity breaches from beginning to end. We could spend a long long time talking about this framework, but instead we’ll explain how our experience with the L33k3rs relates to this framework.
On the first day of camp, you logged into a few websites using a password that you had to discover. In the MITRE Att&ck framework, that is called Credential Access. In other words, you somehow found out the credentials necessary in order to log into those sites that you weren’t supposed to be able to log into.
The first column of the MITRE Att&ck framework is Initial Access. This is pretty much what it sounds like: it’s how the L33k3rs were first able to gain access to the Dessert Database. As we saw yesterday, the L33k3rs uploaded the Hacky File to the Dessert Upload Page and it actually had more files hidden inside of it! With the right code, the L33k3rs were able to vandalize the Dessert Database.
The L33k3rs weren’t the only ones hacking databases, yesterday you hacked the L33k3r database! That time, your initial access into the L33k3r database was carried out through the SQL injection.
There is another column in the MITRE Att&ck framework called Persistence. This is when the hacker is able to stick around in your system even after their initial access. The L33k3rs accomplished this with their nanobots. The L33k3r nanobots hung around the system (they persisted) and continued to cause trouble until you stopped them today!
These are just a few examples of how this past week relates to the real world, but if you explore the MITRE Att&ck framework you could definitely find more connections and learn more specifics about how cybersecurity breaches happen.
Cybersecurity, Continued…
We hope you had a ton of fun this week helping Alice and Bob to stop the L33k3rs, we definitely had fun guiding you through the week! BUT, you don’t have to stop here! This was only the beginning, you can keep learning about cybersecurity and solving cool problems! Here we have compiled some great resources for you if you want to continue learning about cybersecurity. Happy hacking!
- picoCTF is a website with a ton of cyber problems/challenges. They are sorted by category and you definitely have the skills to try these out!
- This XSS Game is all about cross-site scripting (XSS). They involve hacking sites to make them do things they were not intended to do.
- The Terminal that we used this week is available for you to come back to and get more comfortable working in a terminal.
- Here are 2 links about phishing (link 1 and link 2). You may have had time to learn about phishing today, but if you didn’t then you should definitely check out these links! Phishing is one of the ways that hackers gain initial access, and it could happen to you!
- This link will tell you more about SQL Injection so you can do all kinds of cool things when hacking a database.
- These are some SQL Injection practice problems to hone your skills.
- Learnification.fun is our website (created by the UD Cybersecurity Scholars) and you can always revisit the modules we completed this week. Plus, we may add more modules in the future that you can test your skills on.
- The MITRE Att&ck Framework is a super useful table of how cybersecurity breaches are carried out. And to get you started, here is a quizlet on the first column of the MITRE Att&ck Framework: Initial Access.
Here is your badge for completing the Week of Cybersecurity
